The window has a transparent background, which can be quite distracting or confusing (see Figure3), and it’s impossible to reopen the window if it is closed.
The reason for changing the file’s modified time is unclear After the /Users directory is taken care of, it does the same thing to all mounted external and network storage found under /Volumes.. XProtect was how Apple was able to defeat KeRanger, perhaps the most serious Mac-based ransomware threat so far, before it had a chance to become endemic.. Distribution Figure 1 – BitTorrent site distributing Torrent files containing OSX/Filecoder.. Early last week, we have seen a new ransomware campaign for Mac This new ransomware, written in, is distributed via BitTorrent distribution sites and calls itself “Patcher”, ostensibly an application for pirating popular software.
Written in Swift, it is distributed on BitTorrent distribution site as “Patcher” for pirating popular software.. Crypto-ransomware has been very popular lately amongst cybercriminals While most of it targets the Windows desktop, we’ve also seen machines running Linux or macOS being compromised by ransomware in 2016 with, for example, affecting Linux and attacking OS X.. Additionally, the most recent Mac A security researcher has created a free security tool that can detect attempts by ransomware programs to encrypt files on users' Macs and then block them before they do a lot of damage.
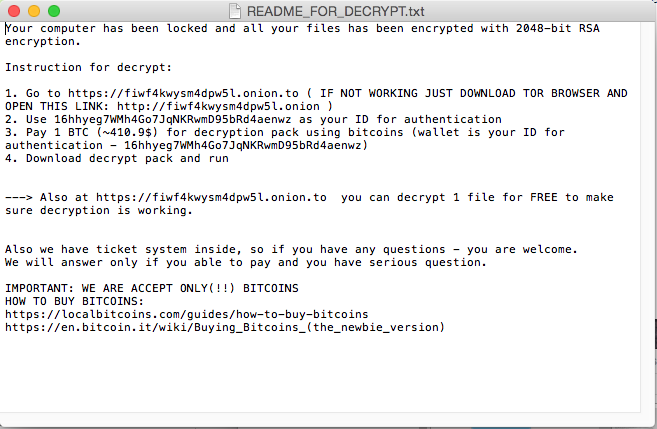

E The Torrent contains a single ZIP file – an application bundle We saw two different fake application “Patchers”: one for Adobe Premiere Pro and one for Microsoft Office for Mac.. Ransomware Not Considered Threat For MacThis last month we have seen a new ransomware for Mac.. Even more about cybersecurity Before the bulk hysteria starts over Apple becoming hacked, let's nip this in the marijuana.. Internal requirements count = 0 size = 12 Figure 3 – The main window of the ransomware File encryption process Clicking the start button – shown in Figure 3 – launches the encryption process.. Finally, the original file is deleted with rm and the encrypted file’s modified time is set to midnight, February 13 th 2010 with the touch command.. In most, if not aIl, of these cases, end customers are having their iCloud balances logged into by unknown events, and these actors have utilized Apple company's Discover My iPhone technology to remotely location a device in Locking mechanism Mode.. It copies a file called README!txt all around the user’s directories such as “Documents” and “Photos”.. The same key is used for all the files, which are enumerated with the find command line tool; the zip tool is then used to store the file in an encrypted archive. 0041d406d9